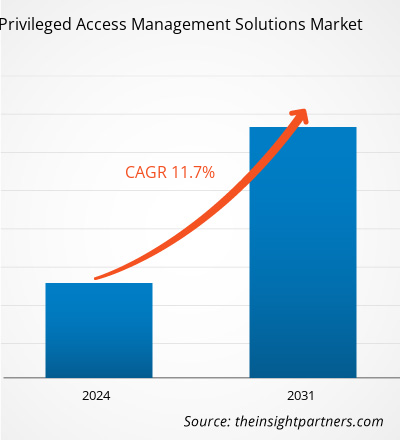
特权访问管理解决方案市场规模预计将从 2023 年的 24.6 亿美元增至 2031 年的 59.5 亿美元。特权访问管理解决方案市场预计在 2023 年至 2031 年期间的复合年增长率为 11.7%。零信任安全模型很可能仍是一个关键的市场趋势。
特权访问管理解决方案市场分析
针对特权帐户和凭据的网络攻击日益盛行,这推动了特权访问管理解决方案的采用。组织越来越意识到需要保护其关键资产免受未经授权的访问和潜在违规行为。PAM 解决方案还通过实施强大的控制和监控特权用户操作,在减轻内部威胁方面发挥着至关重要的作用。此外,PAM 解决方案使组织能够实施考虑实时上下文因素的自适应访问控制,根据特定上下文授予适当的访问权限。这些解决方案还通过提供风险管理功能、维护关键基础设施活动的详细记录以及促进审计友好的 IT 环境,帮助组织满足复杂的合规性要求。
与特权访问滥用相关的安全漏洞数量不断增加,凸显了强大的特权访问管理 (PAM) 解决方案的重要性。这些解决方案通过限制特权帐户成员资格和最小化特权来帮助组织减少攻击面。它们还通过控制和监控特权用户活动来帮助减轻内部威胁。此外,PAM 解决方案使组织能够实施基于上下文的访问控制并增强对复杂法规的遵守。
特权访问管理解决方案市场概览
特权访问管理 (PAM) 解决方案是一种先进的安全措施,旨在通过主动监控、检测和防止未经授权访问关键资源来保护组织免受网络威胁。这些解决方案主要侧重于保护特权账户,这些账户在组织的系统和网络中拥有较高的访问权限,使其成为网络犯罪分子的主要目标。PAM 解决方案利用流程和技术的组合来全面了解特权用户的活动及其对特权账户的使用情况。
定制此报告以满足您的需求
您可以免费定制任何报告,包括本报告的部分内容、国家级分析、Excel 数据包,以及为初创企业和大学提供优惠和折扣
- 获取此报告的关键市场趋势。这个免费样品将包括数据分析,从市场趋势到估计和预测。
特权访问管理解决方案市场驱动因素和机遇
网络攻击次数增加有利于市场Cyberattacks to Favor Market
近年来,企业面临着持续的网络攻击威胁。根据 Embroker Insurance Services LLC 的数据,网络攻击被认为是 2020 年第五大风险,随着技术进步,此类案件数量持续增加。计算机恶意软件、数据泄露和拒绝服务 (DoS) 是网络攻击的几个例子。在 COVID-19 疫情期间,网络犯罪分子利用了企业转向远程工作环境时错位的网络。根据 OneLogin 的数据,2020 年,全球网络犯罪造成的损失超过 1 万亿美元,37% 的组织受到勒索软件的影响,61% 的组织受到恶意软件攻击的影响。2019 年至 2020 年间,美国的网络攻击增加了 139%,2020 年第三季度美国共发生 1.452 亿起此类攻击。与 2019 年相比,2020 年恶意软件攻击增加了 358%。同样,根据 Clusit 报告,2021 年全球网络攻击比上一年增加了 10%。例如,根据 AAG 的数据,2022 年英国每百万互联网用户的网络犯罪受害者人数最多(4,783 名用户),比 2020 年的数字增加了 40%。 2022 年网络攻击的平均成本为 435 万美元,预计到 2025 年这一价值将达到 10.5 万亿美元。
随着各种组织继续在数字环境中运营,网络威胁被视为主要问题。它们对个人、公司和政府产生严重后果。网络攻击数量的增加增加了网络安全对保护关键基础设施和确保个人和组织安全的重要性。组织越来越意识到需要保护其关键资产免受未经授权的访问和潜在入侵。因此,网络攻击数量的增加是推动特权访问管理 (PAM) 解决方案市场增长的重要因素。
基于智能的特权访问管理解决方案的出现
基于情报的 PAM 支持基于风险的访问控制,其中访问决策基于风险评估。评估用户角色、权限和上下文信息等因素以确定与特定访问请求相关的风险级别。这使组织能够实施适应不断变化的风险状况的动态访问控制。基于情报的 PAM 解决方案可以自动响应安全事件或策略违规。例如,如果未经授权的用户试图访问特权帐户,该解决方案可以自动阻止访问尝试并通知安全团队。基于情报的 PAM 解决方案持续实时监控特权访问活动。这种主动监控可帮助组织检测可疑或未经授权的行为,并在潜在安全威胁升级之前做出响应。基于情报的 PAM 还支持自适应访问策略,可根据上下文信息进行动态调整。例如,如果用户的行为表明风险较高,该解决方案可以实施更严格的访问控制或要求采取额外的身份验证措施。因此,基于情报的 PAM 解决方案的出现预计将为特权访问管理 (PAM) 解决方案市场提供巨大的增长机会。
特权访问管理解决方案市场报告细分分析
有助于得出特权访问管理解决方案市场分析的关键部分是产品、部署、企业规模和最终用途行业。
- 根据产品,市场分为解决方案和服务。解决方案部分在 2023 年占据了更大的市场份额。
- 根据部署方式,市场分为云和本地部署。2023 年,云部署占据市场主导地位。
- 就企业规模而言,市场分为大型企业和中小型企业。大型企业在 2023 年占据了市场主导地位。
- 根据最终用途行业,市场细分为 BFSI、IT 和电信、医疗保健、能源和公用事业、零售和电子商务、制造业、政府和国防等。BFSI 部门在 2023 年占据了市场主导地位。
特权访问管理解决方案市场份额(按地区)分析
- 特权访问管理解决方案市场分为五大区域:北美、欧洲、亚太地区 (APAC)、中东和非洲 (MEA) 以及南美和中美。2023 年,北美占据市场主导地位,其次是欧洲和亚太地区。
- 北美是技术创新和先进技术采用方面增长最快的地区之一。随着数字化在各个行业的渗透率不断提高,特权访问管理解决方案已成为北美企业建立安全措施的重要组成部分。随着数字化在各个行业的渗透率不断提高,PAM 解决方案已成为业务的重要组成部分。此外,该地区拥有 IBM Corporation、Microsoft、Broadcom Inc.、Fortinet Inc. 和 One Identity 等市场参与者。
特权访问管理解决方案市场区域洞察
Insight Partners 的分析师已详尽解释了预测期内影响特权访问管理解决方案市场的区域趋势和因素。本节还讨论了特权访问管理解决方案市场在北美、欧洲、亚太地区、中东和非洲以及南美和中美的细分市场和地理位置。
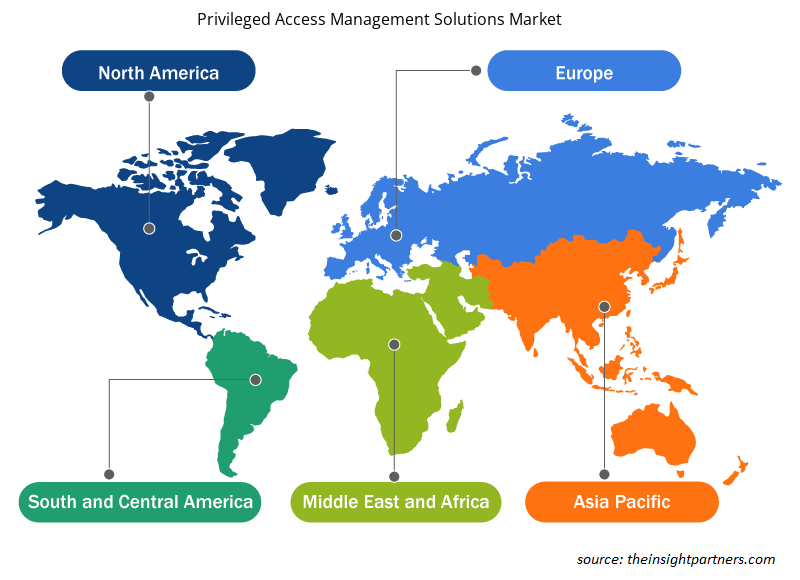
- 获取特权访问管理解决方案市场的区域特定数据
特权访问管理解决方案市场报告范围
| 报告属性 | 细节 |
|---|---|
| 2023 年的市场规模 | 24.6亿美元 |
| 2031 年市场规模 | 59.5亿美元 |
| 全球复合年增长率(2023 - 2031) | 11.7% |
| 史料 | 2021-2022 |
| 预测期 | 2024-2031 |
| 涵盖的领域 | 通过奉献
|
| 覆盖地区和国家 | 北美
|
| 市场领导者和主要公司简介 |
|
市场参与者密度:了解其对商业动态的影响
特权访问管理解决方案市场正在快速增长,这得益于最终用户需求的不断增长,而这些需求又源于消费者偏好的不断变化、技术进步以及对产品优势的认识不断提高等因素。随着需求的增加,企业正在扩大其产品范围,进行创新以满足消费者的需求,并利用新兴趋势,从而进一步推动市场增长。
市场参与者密度是指在特定市场或行业内运营的企业或公司的分布情况。它表明在给定市场空间中,相对于其规模或总市场价值,有多少竞争对手(市场参与者)存在。
在特权访问管理解决方案市场运营的主要公司有:
- 博通公司
- CyberArk 软件有限公司
- 国际商业机器公司
- Okta公司
- 一个身份有限责任公司。
- Delinea 公司
免责声明:上面列出的公司没有按照任何特定顺序排列。
- 获取特权访问管理解决方案市场顶级关键参与者概述
特权访问管理解决方案市场新闻和最新发展
特权访问管理解决方案市场通过收集主要和次要研究后的定性和定量数据进行评估,其中包括重要的公司出版物、协会数据和数据库。特权访问管理解决方案市场的一些发展如下所列:
- 身份安全公司 CyberArk 宣布,全球供应链管理服务公司 FM Logistic 选择了 CyberArk 身份安全平台来保护全球数以万计的身份,并为其数字化转型和信息安全提供安全基础。为了简化流程并提高生产力,FM Logistics 启动了一项重大的数字化转型计划,其中包括云迁移项目。然而,其现有的身份管理解决方案在管理特权身份时需要大量劳动力,并且与其云迁移工作不兼容。该公司需要一种解决方案来降低复杂性、简化和自动化其身份生命周期管理、提供特权访问管理并与云迁移集成。
(来源:CyberArk,新闻稿,2024 年 5 月)
- IBM 推出了新的安全套件,旨在统一和加速整个事件生命周期内安全分析师的体验。IBM Security QRadar Suite 代表了 QRadar 品牌的重大发展和扩展,涵盖了所有核心威胁检测、调查和响应技术,并对整个产品组合的创新进行了重大投资。
(来源:IBM,新闻稿,2023 年 4 月)
特权访问管理解决方案市场报告覆盖范围和交付成果
“特权访问管理解决方案市场规模和预测(2021-2031 年)”对市场进行了详细分析,涵盖以下领域:
- 特权访问管理解决方案市场规模以及范围涵盖的所有关键细分市场的全球、区域和国家/地区预测
- 特权访问管理解决方案市场趋势以及市场动态,如驱动因素、限制因素和关键机遇
- 详细的 PEST 和 SWOT 分析
- 特权访问管理解决方案市场分析涵盖关键市场趋势、全球和区域框架、主要参与者、法规和最新市场发展
- 行业格局和竞争分析,涵盖市场集中度、热图分析、知名参与者以及特权访问管理解决方案市场的最新发展
- 详细的公司简介
- Historical Analysis (2 Years), Base Year, Forecast (7 Years) with CAGR
- PEST and SWOT Analysis
- Market Size Value / Volume - Global, Regional, Country
- Industry and Competitive Landscape
- Excel Dataset

Report Coverage
Revenue forecast, Company Analysis, Industry landscape, Growth factors, and Trends
Segment Covered
This text is related
to segments covered.

Regional Scope
North America, Europe, Asia Pacific, Middle East & Africa, South & Central America
Country Scope
This text is related
to country scope.
Frequently Asked Questions
The key players, holding majority shares, in privileged access management (PAM) solutions market includes Microsoft Corp, International Business Machines Corp, Oracle Corp, Broadcom Inc, and Fortinet Inc.
The North America held the largest market share in 2023, followed by Europe and Asia Pacific.
Asia Pacific is anticipated to grow with the highest CAGR over the forecast period 2024-2031.
Rise of cloud-based privileged access management solutions and zero trust security model is the future trends of the privileged access management (PAM) solutions market.
Increase in number of cyberattacks, rise in demand for protection against insider threats, and stringent government regulations are the driving factors impacting the privileged access management (PAM) solutions market.
The privileged access management (PAM) solutions market was valued at US$ 2.46 billion in 2023 and is projected to reach US$ 5.95 billion by 2031; it is expected to grow at a CAGR of 11.7% during 2023–2031.
Trends and growth analysis reports related to Technology, Media and Telecommunications : READ MORE..
The List Oof Companies - Privileged Access Management (PAM) Solutions Market
- Broadcom Inc.
- CyberArk Software Ltd.
- International Business Machines Corp
- Okta Inc
- One Identity LLC.
- Delinea Inc.
- BeyondTrust Corporation
- Microsoft Corp
- Fortinet Inc.
- Persistent Systems Ltd.
The Insight Partners performs research in 4 major stages: Data Collection & Secondary Research, Primary Research, Data Analysis and Data Triangulation & Final Review.
- Data Collection and Secondary Research:
As a market research and consulting firm operating from a decade, we have published and advised several client across the globe. First step for any study will start with an assessment of currently available data and insights from existing reports. Further, historical and current market information is collected from Investor Presentations, Annual Reports, SEC Filings, etc., and other information related to company’s performance and market positioning are gathered from Paid Databases (Factiva, Hoovers, and Reuters) and various other publications available in public domain.
Several associations trade associates, technical forums, institutes, societies and organization are accessed to gain technical as well as market related insights through their publications such as research papers, blogs and press releases related to the studies are referred to get cues about the market. Further, white papers, journals, magazines, and other news articles published in last 3 years are scrutinized and analyzed to understand the current market trends.
- Primary Research:
The primarily interview analysis comprise of data obtained from industry participants interview and answers to survey questions gathered by in-house primary team.
For primary research, interviews are conducted with industry experts/CEOs/Marketing Managers/VPs/Subject Matter Experts from both demand and supply side to get a 360-degree view of the market. The primary team conducts several interviews based on the complexity of the markets to understand the various market trends and dynamics which makes research more credible and precise.
A typical research interview fulfils the following functions:
- Provides first-hand information on the market size, market trends, growth trends, competitive landscape, and outlook
- Validates and strengthens in-house secondary research findings
- Develops the analysis team’s expertise and market understanding
Primary research involves email interactions and telephone interviews for each market, category, segment, and sub-segment across geographies. The participants who typically take part in such a process include, but are not limited to:
- Industry participants: VPs, business development managers, market intelligence managers and national sales managers
- Outside experts: Valuation experts, research analysts and key opinion leaders specializing in the electronics and semiconductor industry.
Below is the breakup of our primary respondents by company, designation, and region:
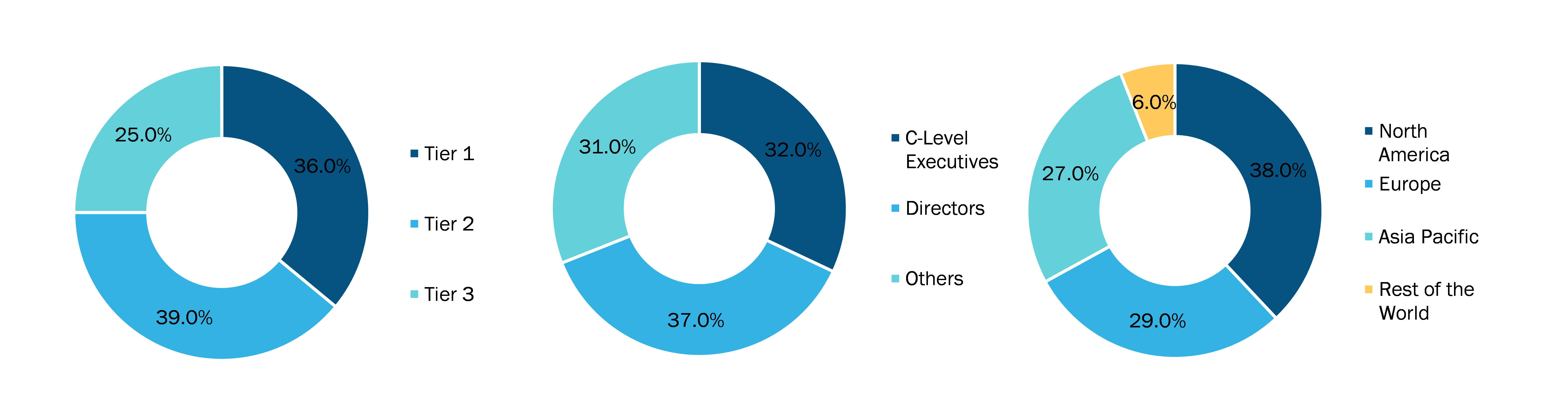
Once we receive the confirmation from primary research sources or primary respondents, we finalize the base year market estimation and forecast the data as per the macroeconomic and microeconomic factors assessed during data collection.
- Data Analysis:
Once data is validated through both secondary as well as primary respondents, we finalize the market estimations by hypothesis formulation and factor analysis at regional and country level.
- Macro-Economic Factor Analysis:
We analyse macroeconomic indicators such the gross domestic product (GDP), increase in the demand for goods and services across industries, technological advancement, regional economic growth, governmental policies, the influence of COVID-19, PEST analysis, and other aspects. This analysis aids in setting benchmarks for various nations/regions and approximating market splits. Additionally, the general trend of the aforementioned components aid in determining the market's development possibilities.
- Country Level Data:
Various factors that are especially aligned to the country are taken into account to determine the market size for a certain area and country, including the presence of vendors, such as headquarters and offices, the country's GDP, demand patterns, and industry growth. To comprehend the market dynamics for the nation, a number of growth variables, inhibitors, application areas, and current market trends are researched. The aforementioned elements aid in determining the country's overall market's growth potential.
- Company Profile:
The “Table of Contents” is formulated by listing and analyzing more than 25 - 30 companies operating in the market ecosystem across geographies. However, we profile only 10 companies as a standard practice in our syndicate reports. These 10 companies comprise leading, emerging, and regional players. Nonetheless, our analysis is not restricted to the 10 listed companies, we also analyze other companies present in the market to develop a holistic view and understand the prevailing trends. The “Company Profiles” section in the report covers key facts, business description, products & services, financial information, SWOT analysis, and key developments. The financial information presented is extracted from the annual reports and official documents of the publicly listed companies. Upon collecting the information for the sections of respective companies, we verify them via various primary sources and then compile the data in respective company profiles. The company level information helps us in deriving the base number as well as in forecasting the market size.
- Developing Base Number:
Aggregation of sales statistics (2020-2022) and macro-economic factor, and other secondary and primary research insights are utilized to arrive at base number and related market shares for 2022. The data gaps are identified in this step and relevant market data is analyzed, collected from paid primary interviews or databases. On finalizing the base year market size, forecasts are developed on the basis of macro-economic, industry and market growth factors and company level analysis.
- Data Triangulation and Final Review:
The market findings and base year market size calculations are validated from supply as well as demand side. Demand side validations are based on macro-economic factor analysis and benchmarks for respective regions and countries. In case of supply side validations, revenues of major companies are estimated (in case not available) based on industry benchmark, approximate number of employees, product portfolio, and primary interviews revenues are gathered. Further revenue from target product/service segment is assessed to avoid overshooting of market statistics. In case of heavy deviations between supply and demand side values, all thes steps are repeated to achieve synchronization.
We follow an iterative model, wherein we share our research findings with Subject Matter Experts (SME’s) and Key Opinion Leaders (KOLs) until consensus view of the market is not formulated – this model negates any drastic deviation in the opinions of experts. Only validated and universally acceptable research findings are quoted in our reports.
We have important check points that we use to validate our research findings – which we call – data triangulation, where we validate the information, we generate from secondary sources with primary interviews and then we re-validate with our internal data bases and Subject matter experts. This comprehensive model enables us to deliver high quality, reliable data in shortest possible time.

 Get Free Sample For
Get Free Sample For